🚀 Experience the new and improved APIVoid! Check out what's new
Our APIs enable your engineering and security teams to identify fake and disposable emails, detect bots and proxy IP addresses, and flag invalid and fake phone numbers in real time. By accessing valuable fraud signals, you can make instant, data-driven decisions and automate workflows to streamline fake account prevention.
IP Address: 193.84.71.23
Checking reputation...
Email: hemider189@cristout(.)com
Checking reputation...
Email: wauzeio534@1secmail(.)website
Checking reputation...
Phone: +13322720602
Checking reputation...
Domain: dqdjescs@wildbmail(.)com
Checking reputation...
Email: info@inexistentdomain(.)com
Checking reputation...
IP Address: 37.187.29.43
Checking reputation...
Email: xetogyhy@thetechnext.net
Checking reputation...
IP Address: 192.42.116.196
Checking reputation...






Fake accounts undermine your platform’s security, inflate metrics, and waste valuable resources. Our intelligence APIs provide key data points, fraud signals, and actionable insights, empowering you to build decisioning systems that efficiently detect and block fraud. Prevent users from creating accounts with fake emails, proxy or known-malicious IP addresses, and fake phone numbers, ensuring your platform is reserved for genuine users.
Check the safety reputation of an IPv4 or IPv6 address using multiple IP address blacklist services.
Check the reputation of a domain (e.g google.com) using multiple domain blacklist services.
Check the safety reputation of an email address, detect temporary emails and suspicious emails.
Validate and normalize a phone number, get location, carrier and line type, detect invalid and fake numbers.
Check the safety reputation and risk score of an URL using unique URL security checks.
Obtain a "trust score" of any website, useful to spot potentially fraudulent and insecure web shops.
Explore a practical workflow to strengthen your signup process by detecting key risk indicators and blocking fake signups using a combination of IP intelligence, anonymity signals, email analysis, with some interesting comments.
// Check the user IP address reputation
$ipReputation = makeAPIVoidRequestV2('/v2/ip-reputation', ['ip' => $ip]);
if (is_array($ipReputation)) {
// What to do if the IP is detected only by 1 or 2 blocklists?
// These may not be definitive indicators of malicious activity but can still suggest potential risk.
// For example, you might choose to apply additional verification steps,
// such as prompting the user for SMS-based phone number verification,
// or requesting business details like company name and intended use case.
if (($ipReputation['blacklists']['detections'] ?? 0) === 1 ||
($ipReputation['blacklists']['detections'] ?? 0) === 2) {
// Apply your verification logic here (e.g., SMS, email challenge, or business form)
}
// Block the IP address if it is detected by 3 or more blocklists.
// A higher number of detections reduces the likelihood of a false positive.
if (($ipReputation['blacklists']['detections'] ?? 0) >= 3) {
// Block the action with a message like "Your IP is detected by 3 or more blocklists".
}
// How to properly handle IPs detected as VPN?
// Depending on your SaaS type (e.g., financial services), you may choose to block VPN users entirely.
// Alternatively, you can allow them but flag their session as VPN-based,
// and optionally restrict certain features, such as limiting access to a free trial plan.
if (($ipReputation['anonymity']['is_vpn'] ?? false) === true) {
// Apply your custom logic here (e.g., block, flag, or restrict features)
}
// How should hosting or data center IPs be handled?
// These IPs may indicate automated signups, bots, or anonymous activity,
// but they are not always inherently malicious and can belong to legitimate users.
// A common approach is to allow these users conditionally by enforcing additional verification,
// such as requiring SMS-based phone verification or collecting company and use case details.
if (($ipReputation['anonymity']['is_hosting'] ?? false) === true) {
// Apply your verification logic here (e.g., SMS challenge or business info form)
}
// Block IP addresses identified as public proxies or Tor traffic.
// These sources are commonly used to mask identity and bypass access controls.
if (($ipReputation['anonymity']['is_proxy'] ?? false) === true ||
($ipReputation['anonymity']['is_tor'] ?? false) === true) {
// Block the action with a message like "Your IP is detected as proxy or Tor".
}
// Do you need to restrict access from specific countries?
// For example, you may choose to block IP addresses originating from certain locations.
if (in_array(($ipReputation['information']['country_code'] ?? ''), ['IT', 'NL'])) {
// Block the action with a message like "Your IP is located in a blocked country".
}
}
// Check the user email address reputation
$emailReputation = makeAPIVoidRequestV2('/v2/email-verify', ['email' => $email]);
if (is_array($emailReputation)) {
// Block suspicious and disposable email addresses.
// These are often used for temporary access or to avoid verification,
// and may indicate fraudulent intent or attempts to abuse trial-based features.
if (($emailReputation['suspicious_email'] ?? false) === true ||
($emailReputation['suspicious_domain'] ?? false) === true ||
($emailReputation['disposable'] ?? false) === true) {
// Block the action with a message like "Email is classified as suspicious".
}
// Do you allow signups with free email addresses on your SaaS?
// If your service targets only businesses, you may choose to block common free email providers.
// This helps maintain a cleaner, business-focused user base as intended.
if (($emailReputation['free_email'] ?? false) === true) {
// Block the action with a message like "Free email addresses are not allowed".
}
// Should you block email domains with risky TLD like .top?
// This approach can reduce signups from suspicious or less common domain sources,
// but it may also result in false positives, affecting legitimate users.
if (($emailReputation['risky_tld'] ?? false) === true) {
return json_encode(['error' => 'Domain TLD is classified as risky.']);
// Alternatively, prompt the user for SMS verification or business info form
}
// Block emails with no MX records configured.
// A missing MX record indicates the domain cannot receive emails,
// which is often a sign of a fake or misconfigured address.
if (($emailReputation['has_mx_records'] ?? true) === false) {
// Block the action with a message like "Email domain cannot receive emails".
}
}
// Check domain age of email domain
$domainAge = makeAPIvoidRequestV2('/v2/domain-age', ['host' => substr(strrchr($email, "@"), 1)]);
if (is_array($domainAge)) {
// Block email addresses from domains registered less than 30 days ago.
// Recently created domains are often linked to suspicious or disposable email activity.
if (($domainAge['domain_age_in_days'] ?? 0) > 0 && ($domainAge['domain_age_in_days'] ?? 0) <= 30) {
// Block the action with a message like "Email domain is too new".
}
}
// Check if email domain is parked
$parkedDomain = makeAPIvoidRequestV2('/v2/parked-domain', ['host' => substr(strrchr($email, "@"), 1)]);
if (is_array($parkedDomain)) {
// Block email addresses is domain is a parked or inactive domain
if (($parkedDomain['parked_domain'] ?? false) === true) {
// Block the action with a message like "Email domain is parked".
}
}Account and API Security
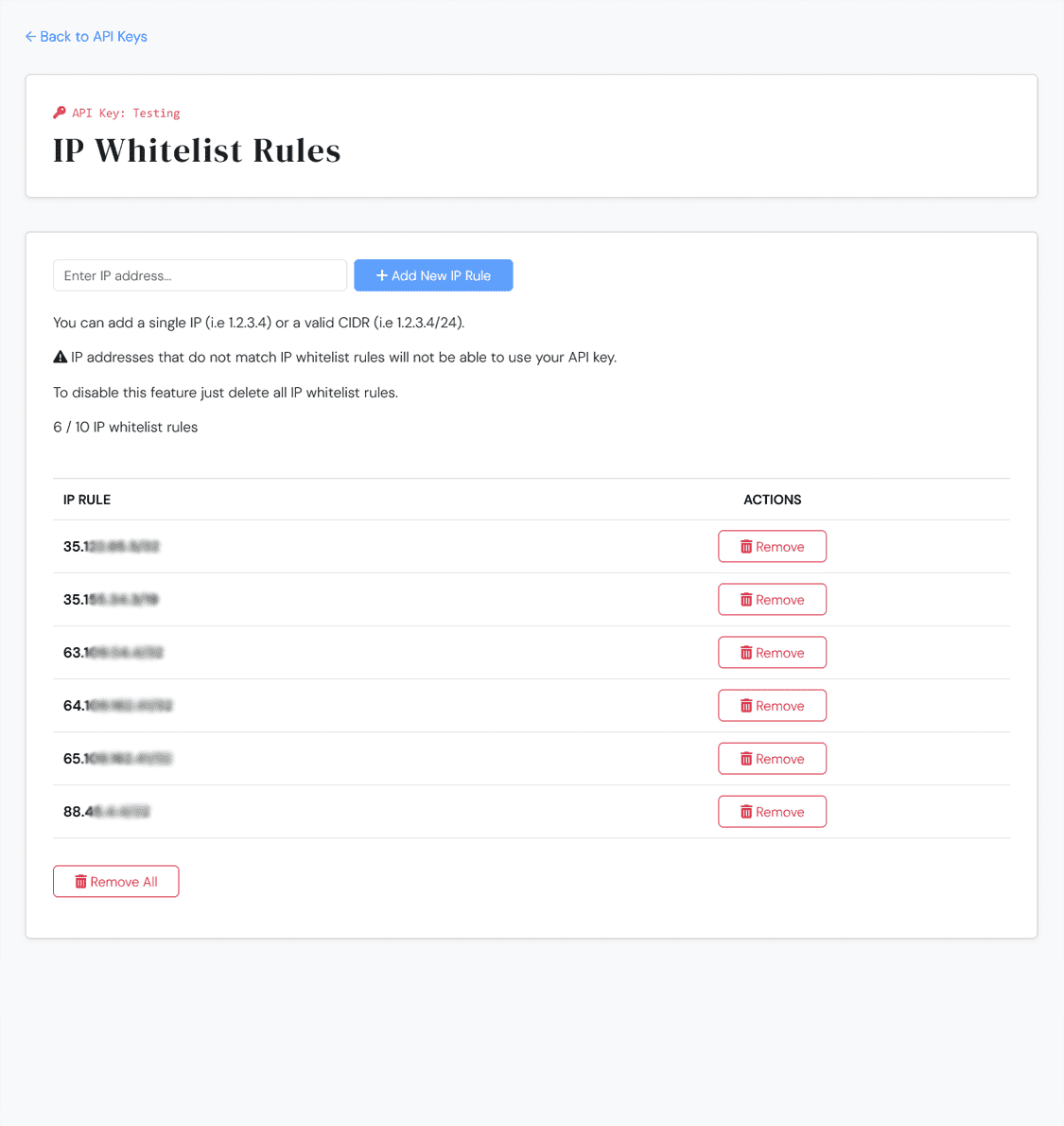
Data sent on the Dashboard account and on our API services is always encrypted (on frontends and backends). We provide options to secure your account with 2FA and your API keys with IP CIDR whitelist.
All traffic on our API services is safely encrypted in transit with HTTPS SSL (TLSv1.2+) encryption.
Protect your API keys by allowing only trusted CIDR IP addresses and block unknown IP addresses.
You can enable 2FA authentication via Google Authenticator to additionally protect your account.
Your account data is encrypted in transit and at rest by default within Google Cloud Platform.
Key Service Features
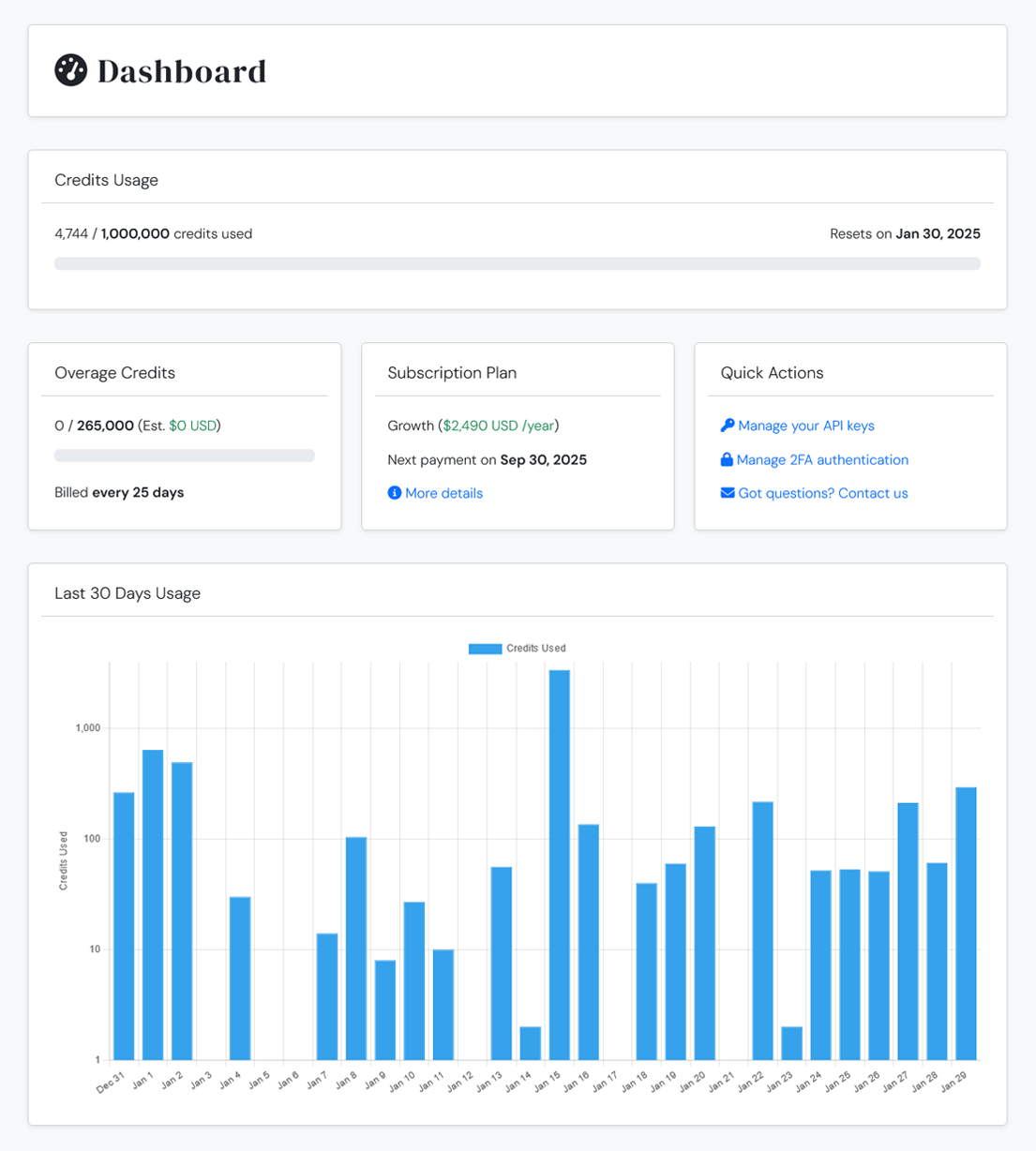
With our service you can: use one or more APIs within your subscription, manage multiple API keys, customize the overages and more. Choose the right plan with the help of our pricing calculator.
Within your subscription you have access to all our 20+ (and growing) threat intelligence APIs.
We provide automated monthly or yearly subscription plans. With a yearly plan you get 2 months free.
Starting with the Startup plan, you can enable overages option to extend your monthly plan credits.
Based on your plan, you can manage multiple API keys (such as one for Production and one for Testing).
Create your account, pick a subscription plan, and make your first API call instantly with your API key—simple as that!
Get started now